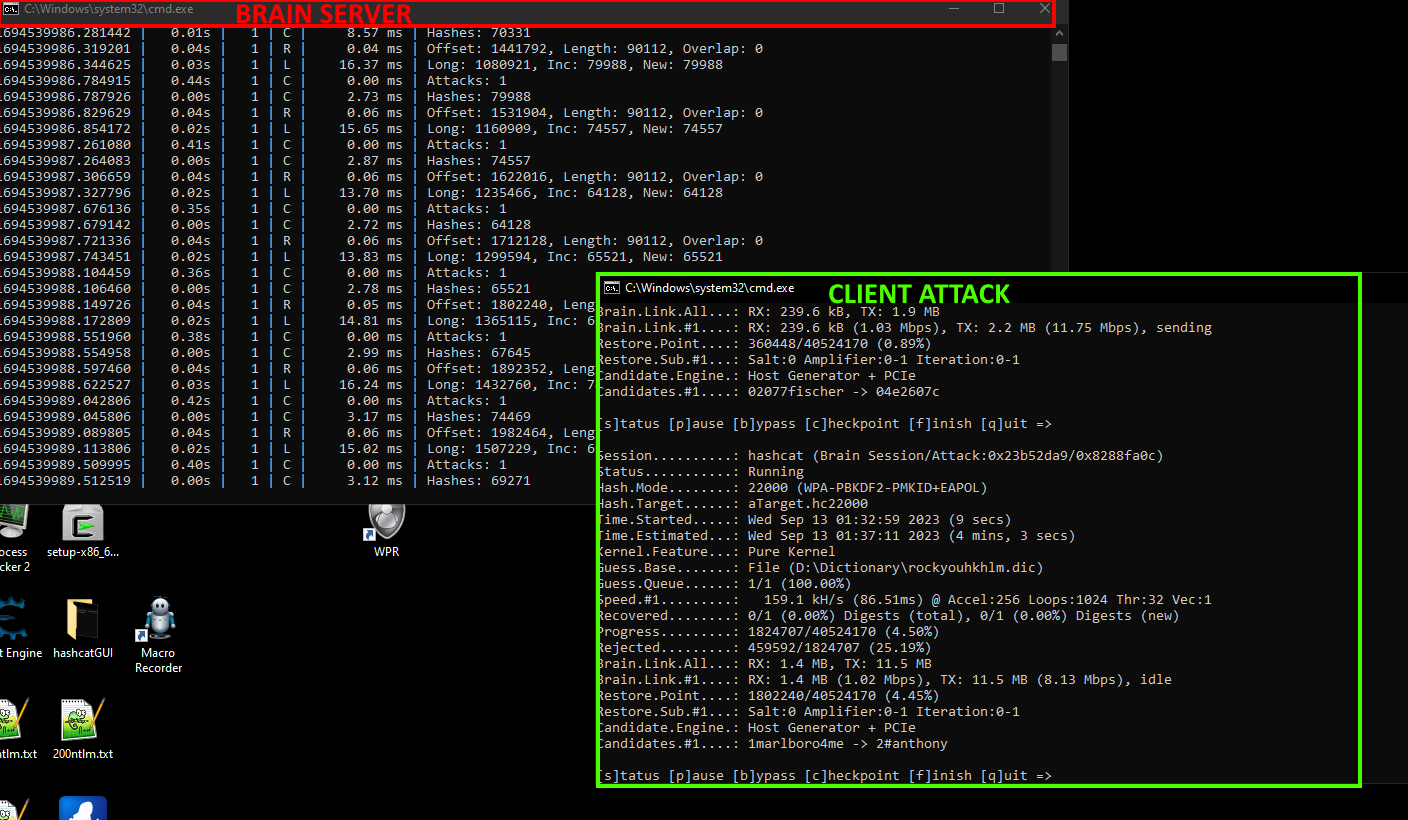
We're proud to announce the release of hashcat v7.0.0, the result of over two years of development, hundreds of features and fixes, and a complete refactor of several key components. This version also includes all accumulated changes from the v6.2.x minor releases.
This release is huge. If you have 30 minutes, here's the writeup: Full Release Notes and detailed writeup
Here's a quick summary:
- Over 900,000 lines of code changed
- Contributions from 105 developers, including 74 first-time contributors
- Merged and documented all previously unannounced 6.2.x features
Major New Features
- Assimilation Bridge: Integrate external resources like CPUs, FPGAs, embedded interpreters, and more into the cracking pipeline.
- Python Bridge Plugin: Rapidly implement hash-matching logic in Python. No recompilation needed, supports multithreading and rule engine by default.
- Virtual Backend Devices: Internally partitions physical GPUs into multiple logical devices for better bridge integration and async workloads.
- Hash-Mode Autodetection: Omit the
-mflag and let Hashcat detect the hash-mode, or use--identifyto list possibilities. - Docker Build Support: Build Hashcat in a fully containerized, cross-platform environment, including cross-compilation to Windows.